
Cybersecurity
Showing 0 of X


Beware of PDF Phishing Scams: The New Threat You Need to Know About!

The Ultimate Browser Security Checklist for Chrome, Firefox, and Edge
The Best Tools for Safer Internet Use: VPN, DNS Filters, and Password Managers

Cybersecurity for Remote Workers 2025: The Practical Checklist
Using AI for OSINT: A Practical Step‑by‑Step Playbook

5 Open-Source Dark Web Monitoring Projects You Can Deploy Today

More Than 60% of Enterprise Cybersecurity Incidents Come From Known, Unresolved Risks

Will Autonomous Vehicles Become Your Next Cyber-Security Liability?

Open-Source Malware: How Hackers Weaponize Public Repositories to Breach the Software Supply Chain

Goodbye Passwords? How Passkeys & Biometrics Are Taking Over in 2025

Best Password Managers for 2025

Critical TP-Link Router Vulnerabilities: Active Exploitation and Security Risks
Quantum Leap: How Quantum Computing Will Reshape Cybersecurity Forever

The Alarming Surge in DDoS Attacks: 358% Year-Over-Year Increase Threatens Digital Infrastructure

Record $16.6 Billion Lost to Cybercrime in the US: FBI 2024 Report Insights

WooCommerce Phishing Campaign: How Cybercriminals Exploit Fake Security Alerts

Best Gaming Firewalls for Windows: Secure & Lag-Free in 2025
The Best Antivirus Software for 2025

2FA vs MFA: Understanding Security Differences

How Hackers Use Fake Plugins to Spread Malware on WordPress Sites
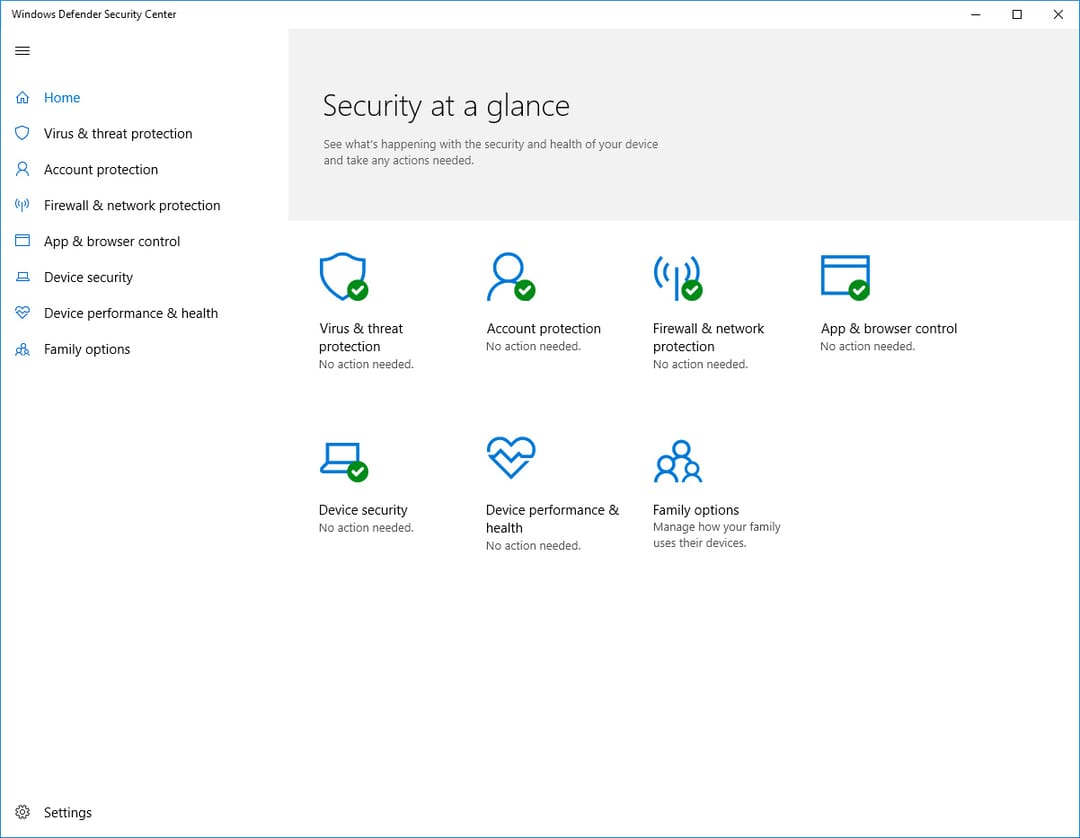
Windows Security vs. Microsoft Defender: Key Differences Explained

Data Breach Hits Internet Archive: Personal Info of 31 Million Users Exposed

Consequences of Password Reuse: Don't Let It Happen to You

From Reactive to Predictive: How AI Anticipates Cyber Threats

The Ultimate OPSEC Guide: Data Protection & Cybersecurity Essentials

Antivirus vs. Security Suites: Which is Right for You?
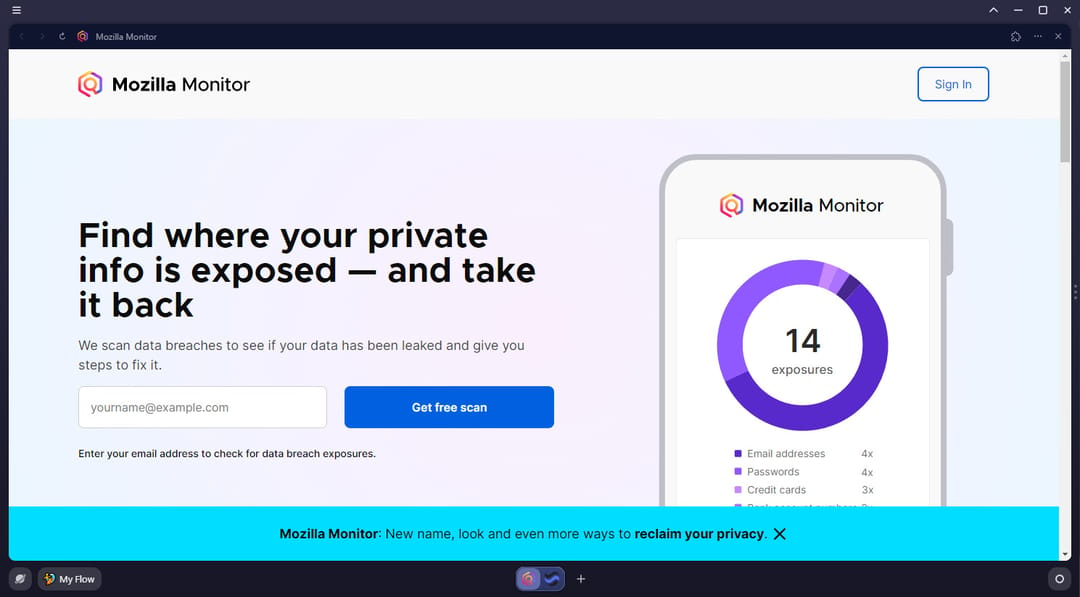
Mozilla Cuts Ties with Data Broker Removal Partner Due to Conflict of Interest

The Most Common Cyberattacks and How To Prevent Them
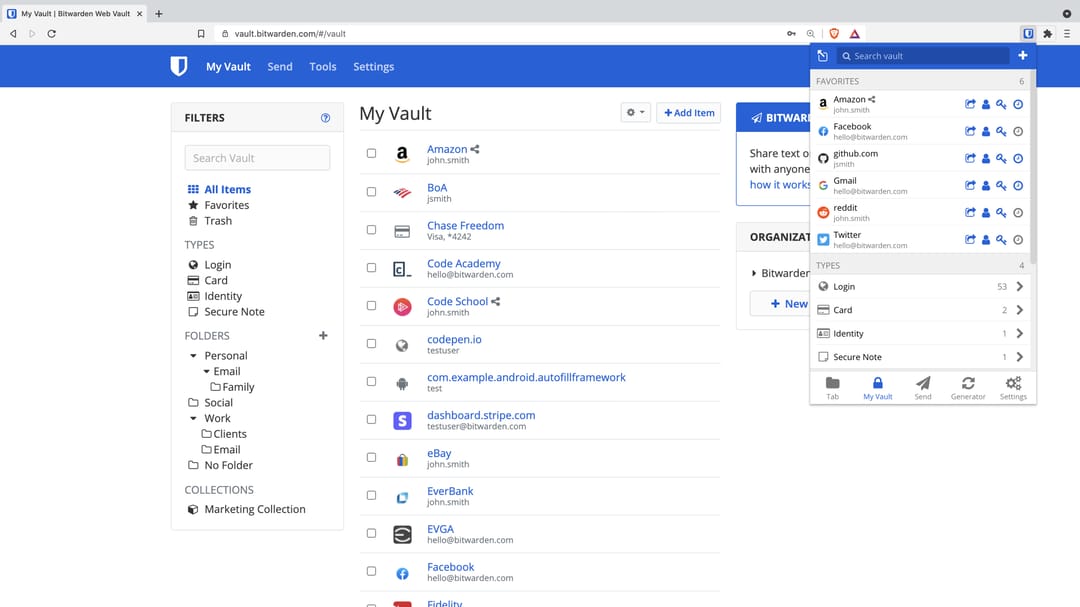
Bitwarden: The Best Open-Source Password Manager in 2024

IP Scanner Tools: What They Are and How to Use Them

Securing Self-Hosted Services in a Home Lab

Cybersecurity Best Practices for Small Businesses

The Rise of VPNs in the Era of Data Privacy

The Role of a SOC Analyst: Responsibilities, Skills, and Salary

The Future of Cybersecurity: Predictions and Preparations
No results found